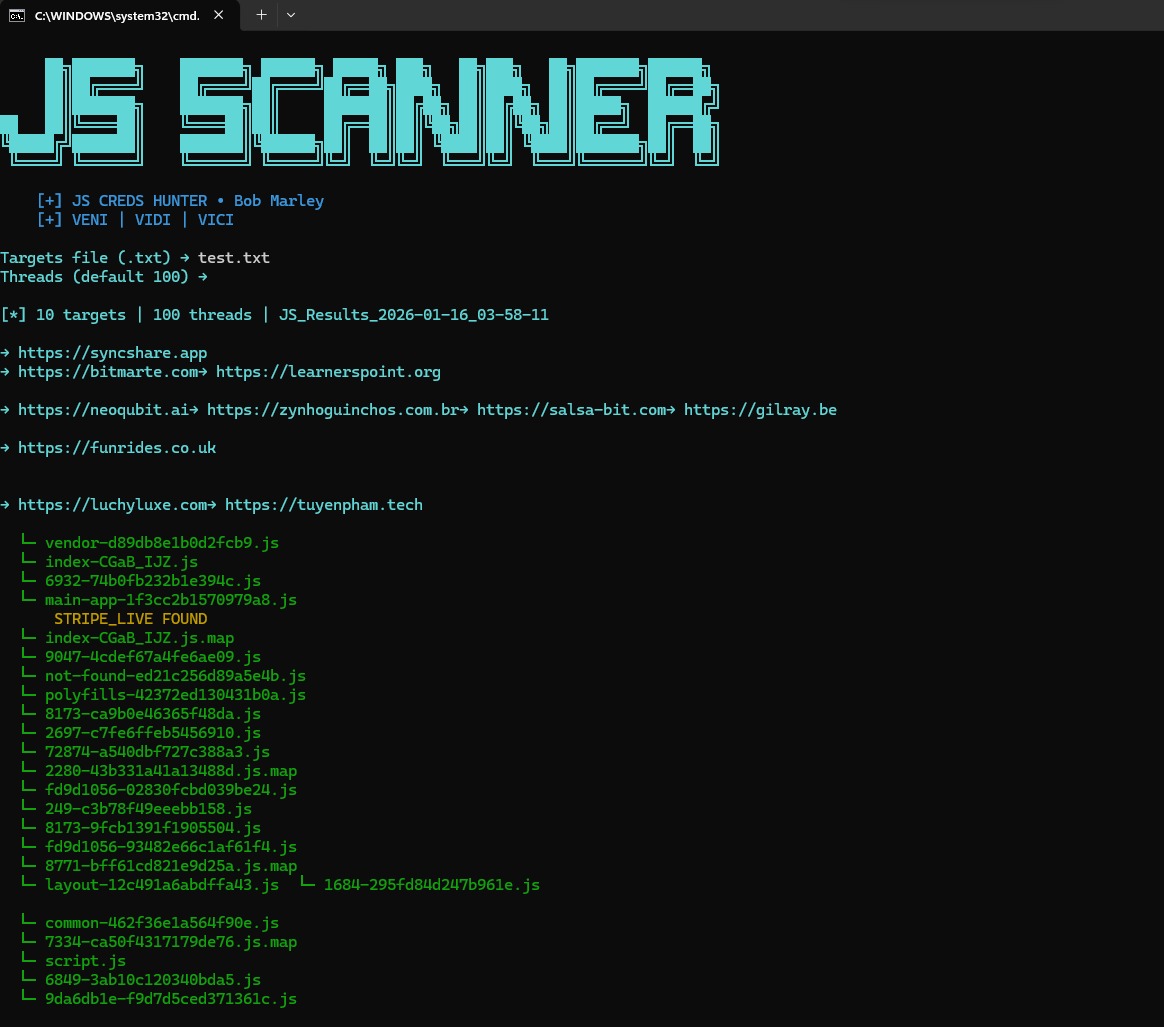
This Python toolkit is designed to hunt for high-value secrets, API keys, and database credentials exposed within JavaScript files found on target web applications.
Automated scanning and extraction of sensitive credentials from JS files (e.g., target.com). Identifies:
- AWS Keys: AKIA/ASIA Access Keys + Secret Keys + Region extraction.
- Stripe: Live secret keys with optional Telegram alerts.
- Database Connection Strings: Validated MongoDB, PostgreSQL, MySQL, Redis, and MSSQL URLs.
- Tokens: GitHub Personal Access Tokens (PAT) and Slack Tokens.
- Target Gathering: Accepts single URLs or lists. Automatically probes for
.js,.ts,.mjs, and.envfiles. - Spidering: Curls the base URL to find scripts via HTML tags and regex-based discovery of hidden paths.
- Logic Gate V4: Filters out "library noise" from common JS libraries like JSEncrypt or RSA components to minimize false positives.
- Validation: Uses entropy checks (V5 logic) to ensure detected AWS secret keys are genuine and not random garbage.
- Notification: Integrates with Telegram API to send real-time alerts when Stripe Live keys are discovered.
pip3 install requests beautifulsoup4 coloramapython3 main.py- Enter targets file:
targets.txt - Enter threads:
100(default)
Piped: echo "targets.txt\n100" | python3 main.py
Results are organized in a timestamped directory JS_Results_YYYY-MM-DD_HH-MM-SS/:
RESULT-AWS.txt: Formatted AWS credentials.RESULT-STRIPE.txt: Stripe secret keys.RESULT-DB.txt: Database connection strings.RESULT-TOKENS.txt: GitHub and Slack tokens.fingerprinted.txt: List of processed URLs.
requests
beautifulsoup4
colorama
pip install requests beautifulsoup4 colorama
For authorized penetration testing & educational purposes only (user confirmed permission under ToS). Unauthorized use illegal/unethical.
Buy me a Coffee:
₿ BTC: 17sbbeTzDMP4aMELVbLW78Rcsj4CDRBiZh
©2025 khadafigans